KEV Vulnerabilities Table
The KEV Vulnerabilities table shows a list of KEV vulnerabilities detected by the VTM service for a particular client depending on the most recent scan group.
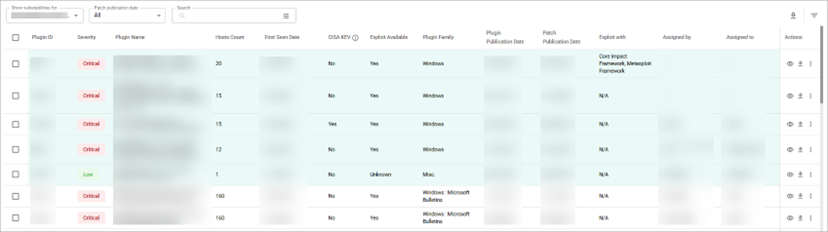
In the KEV Vulnerabilities table, the information is grouped into the following columns:
- Plugin ID—a unique identification number of a plugin.
- Severity—a categorization of the risk and urgency of a KEV vulnerability (Critical, High, Medium, or Low).
- Plugin Name—a title of a plugin.
- Hosts Count—the number of hosts affected by a KEV vulnerability.
- First Seen Date—the date when a KEV vulnerability was first detected.
- Related CVE—the CVE identifier associated with the KEV vulnerability.
- Ransomware Campaign Use—shows whether the KEV vulnerability has been linked to known ransomware campaigns.
- Product—the software or system in which the KEV vulnerability exists.
- Assigned to—shows a user who was assigned to work on the KEV vulnerability.
- Date Added to KEV—the date the vulnerability was added to CISA’s KEV.
- Actions—shows the following actions:
- View details—you can view the detailed information about a KEV vulnerability from the list (see View KEV Vulnerability Details).
- Download vulnerability—you can download information about a KEV vulnerability from the list (see Download KEV Vulnerabilities Information).
- The Assign icon with which you can assign a KEV vulnerability to a user who will work on it (see Assign KEV Vulnerability).
- The Ask question icon with which you can ask a question about the KEV vulnerability.
- The Suppress icon with which you can suppress selected vulnerability.
- The Add to Risk Register icon with which you can add vulnerability to the Risk Register.
Related Topics
Select KEV Vulnerabilities Patch Publication Date
Filter KEV Vulnerabilities List