Suppressed Vulnerabilities Table
The Suppressed Vulnerabilities table shows a list of accepted vulnerabilities detected by the VTM service for a particular client depending on the patch publication date.
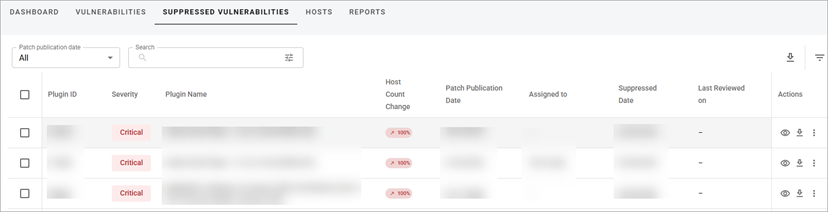
In the Suppressed Vulnerabilities table, the information is grouped into the following columns:
- Plugin ID—a unique identification number of a plugin.
- Severity—a categorization of the risk and urgency of a vulnerability (Critical, High, Medium, Low).
- Plugin Name—a title of a plugin.
- First Seen Date—the date when the vulnerability was first detected.
- CISA KEV—shows whether a vulnerability is related to the CISA KEV list.
- Note: CISA’s Known Exploited Vulnerabilities (KEV) catalog is an authoritative list of vulnerabilities confirmed to be actively exploited in the wild. Maintained by CISA, the KEV catalog is a key resource for prioritizing remediation based on real-world threat activity.
- Host Count Change—the percentage change of the number of affected hosts in the latest scan group compared to the previous scan group.
- Patch Publication Date—a date when a vendor published a patch for an accepted vulnerability.
- Assigned to—shows a user who was assigned to work on the vulnerability.
- Suppressed Date—shows the date when the vulnerability was suppressed.
- Last Reviewed On—shows the date when the vulnerability was last reviewed.
- Actions—shows the following actions:
- View more—you can view the detailed information about a vulnerability from the list (see View Vulnerability Details).
- Download vulnerability—you can download information about a vulnerability from the list (see Download Vulnerabilities Information).
- Other—you can view the hidden actions:
- The Assign icon with which you can assign a vulnerability to a user who will work on it (see Assign Vulnerability).
- The Ask a question icon with which you can ask a question about the vulnerability.
- The Unsuppress icon with which you can cancel the suppression of the vulnerability. Once the vulnerability is unsuppressed, it will be available on the Vulnerabilities page again.
- Note: The vulnerabilities with the unanswered questions are highlighted in green and can be found at the top of the table.
Related Topics
Suppressed Vulnerabilities Tab
Search Suppressed Vulnerabilities
Filter Suppressed Vulnerabilities List
View Suppressed Vulnerability Details